╔════════════════════════════════════════════════════════════════════════════╗
║ The Minimalist Living CTF #1 ║
║ by lessismore1337 ║
║ ║
║ Perfection is achieved, not when there is nothing more to add, but when ║
║ there is nothing left to take away. ― Antoine de Saint-Exupéry ║
║ ║
║ This minimalistic CTF challenge truly embodies the philosophy of "less ║
║ is more." It is written in a custom assembly code that runs on a ║
║ virtual machine, which is itself written in C++. The objective is to ║
║ reverse engineer the virtual machine and discover the hidden flag. ║
║ Although the challenge is small in size, don't be fooled – it is far ║
║ from easy. Solving it will require a combination of advanced skills, ║
║ determination, and a meticulous eye for detail. Good luck! ║
║ ║
║ File:.........mlctf1.exe ║
║ Size:.........217KB (statically linked) ║
║ Date:..YMD....2022-12-16 ║
║ Difficulty:...4/10 ║
║ CRC32:........0x2A011FE8 ║
║ MD5:..........0x89ED57FB2352263A2D1C874A7F2CDDD6 ║
║ SHA1:.........0xB08BA7CBDD23C63D3D1F3D14296BC3CE0D325BA9 ║
║ ║
║ For more information, please visit ║
║ https://minimalistliving.neocities.org/posts/the-minimalist-living-ctf-1 ║
║ ║
╚════════════════════════════════════════════════════════════════════════════╝
Hello, fellow minimalists! We are looking for highly intelligent individuals. To find them, we have devised a test. Introducing the first ever Minimalist Living Capture The Flag (CTF) challenge!
A Capture The Flag (CTF) is a type of computer security competition wherein participants engage in unraveling diverse puzzles and deciphering codes to uncover concealed flags. These flags typically manifest as text strings, serving as evidence of successfully overcoming the challenge. CTFs not only offer an entertaining experience but also serve as an educational and rewarding pursuit, fostering valuable skills such as problem-solving, critical thinking, and creativity.
The first Minimalist Living CTF #1 stands out as a distinctive challenge conceived by one of our Minimalist Living team members, lessismore1337. As a proficient programmer and a fervent minimalist, he has crafted a challenge aligned with the minimalist philosophy: less equals more. This challenge exudes simplicity, elegance, and complexity, serving as a means to assess and enhance your knowledge, skills, and patience.
Download Link
If you want to do this challenge without any further knowledge, here is the download link:
If you want to learn more about the challenge, keep reading. But be warned: there are spoilers ahead!
Challenge Details
The challenge is a single executable file, written in C++. You may wonder why C++, since I have said many times that C++ is bad. Well, I have changed my mind. C++ is actually a great language for minimalism, if used properly. It allows you to write efficient, expressive, and elegant code, with minimal overhead. Stay tuned for a blog post about my latest revelations.
Returning to the challenge at hand, it’s important to note that the challenge itself is not technically written in C++. Instead, it is written in a custom assembly code developed by lessismore1337 specifically for the virtual processor, which itself is written in C++. It’s worth highlighting that the virtual machine is exclusively relying on the standard library without any reliance on external libraries or frameworks.
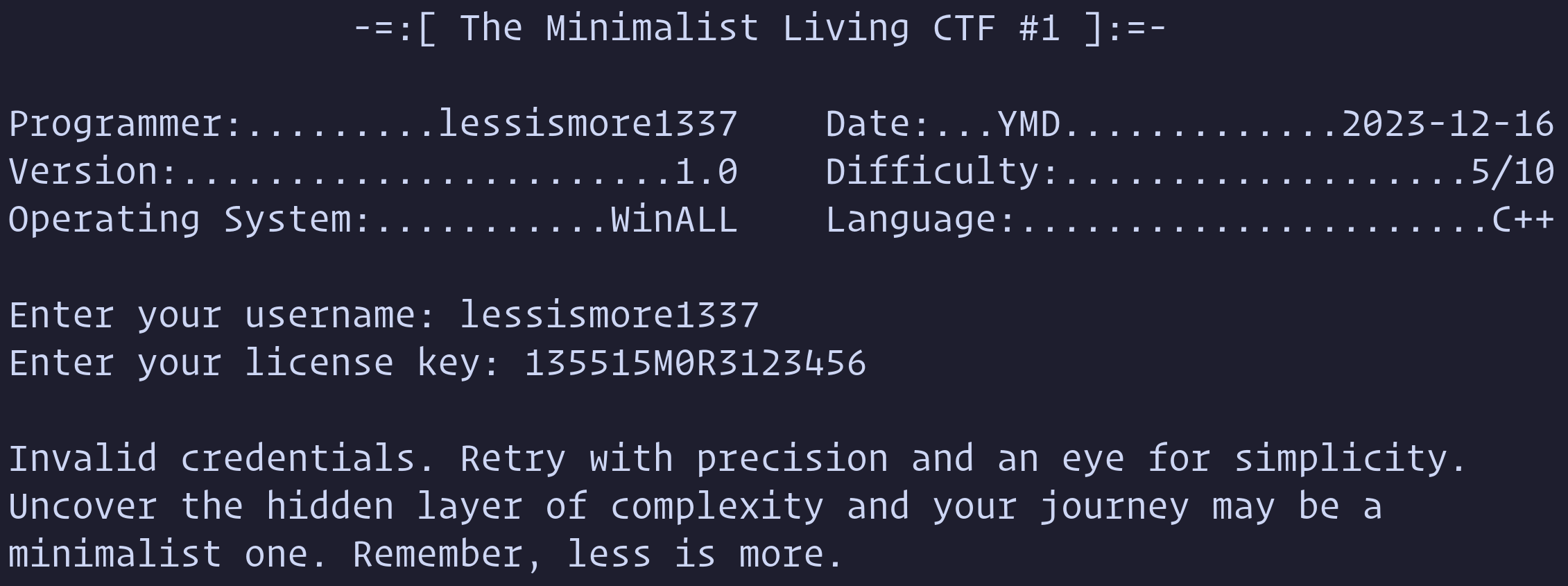
When running the challenge, it first prompts for user input. After the user enters their name, it generates a unique key for the user, which is obfuscated and never stored in memory in plain text. Once the key is generated, the program then requests the license key. Upon entering the license key, the program verifies it, and if it matches the correct key’s structure, the key’s properties are used to decrypt the good message containing the flag. This means that even if you discover where the good message is displayed and attempt to redirect the program flow there prematurely, the VM registers and stack must contain the appropriate properties derived from the license key for the decryption to be successful.
This entire functionality is implemented using custom assembly code that the virtual machine executes. The virtual machine includes a stack, a few registers, and flags. The virtual machine is relatively complex and requires significant knowledge about reverse engineering and how virtual machines are used to obfuscate code, among other things. For this reason, I would rate this challenge a four or five out of ten on the difficulty scale. A level one challenge would be a simple strcmp() operation with a subsequent jump to the positive message. In contrast, a level ten challenge would resemble the complexity of a sophisticated commercial anti-tamper solution such as Denuvo.
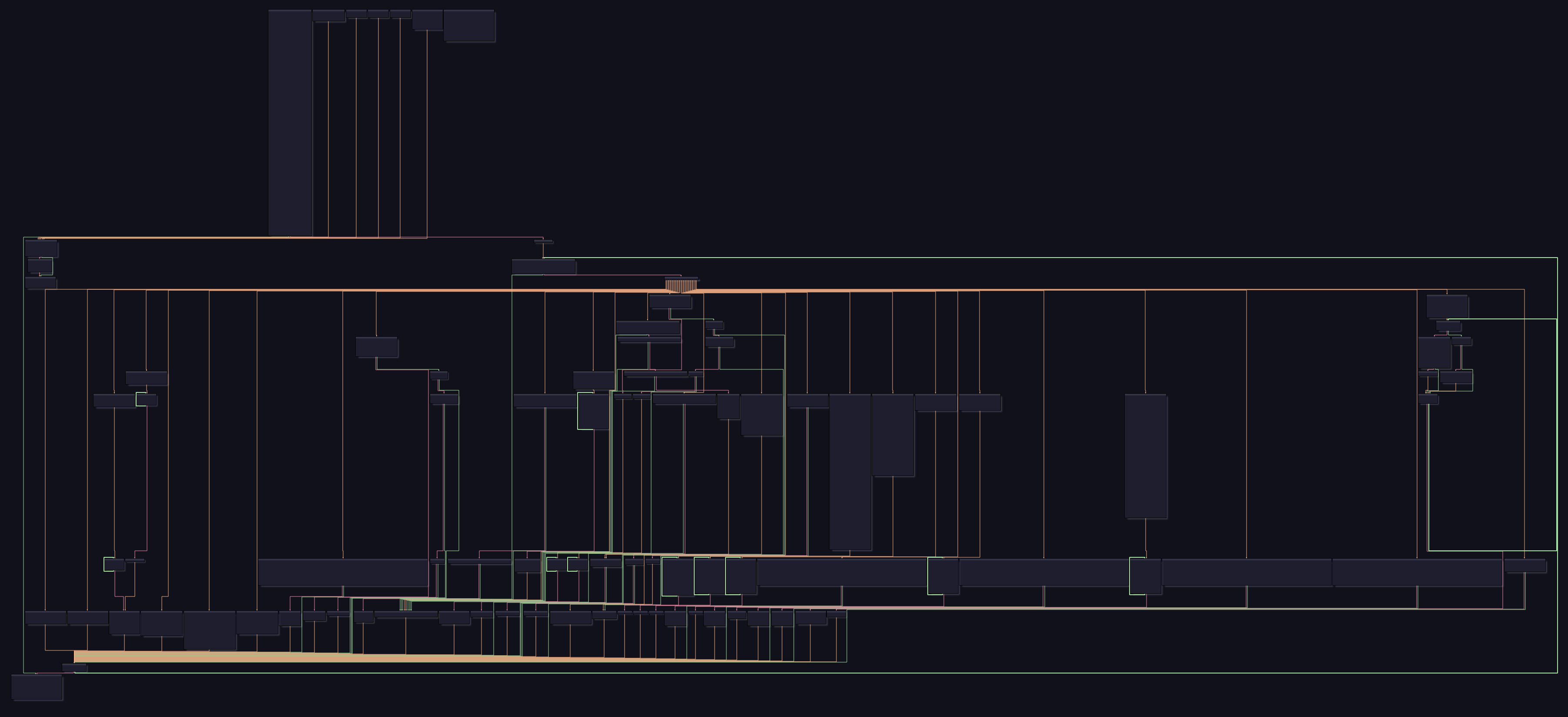
Goals
The primary objective of the challenge is to successfully find the flag. Achieving this requires a throughout analysis of the virtual machine, followed by the adept decryption of the flag. Participants are granted the flexibility to employ any tools or methods they deem fit. It is crucial to emphasize that the challenge is intentionally designed for resolution through the application of reverse engineering skills, eschewing brute force or speculative approaches.
For seasoned Capture The Flag (CTF) enthusiasts, an additional task awaits: the creation of a keygen. A keygen, in this context, refers to a program tasked with generating a valid license key for the challenge. The keygen should embody simplicity and conciseness, adhering to the minimalist principle with the understanding that, in this context, less truly equates to more.
Conclusion
We hope you enjoy the Minimalist Living CTF #1. This is a challenge that we created with passion and care, and we hope it resonates with the minimalist spirit. It is not flashy, or easy. It is a test of your intelligence, abilities, and perseverance. It is also a learning opportunity, where you can develop skills such as problem-solving, critical thinking, and creativity.
If you want to share your thoughts, opinions, or feedback, please feel free to reach out to me or lessismore1337. We are eager to hear from you. And if you succeed in cracking the challenge, or writing a keygen, please show us your solutions. We are curious to see how you tackled the challenge, and what you gained from it.
Thank you for reading, and happy hacking!